How to spot a phishing message and what to do can be one of the most important things you will ever do online. Have you ever received a message that had an urgent tone from someone claiming to be a bank or credit card company or a text from a number not in your contacts asking an odd question, “John, do you still teach diving?”?
That second one is odd right?? It is very odd if you never dove before and your name is not John. These are examples of phishing.
What is phishing?
Phishing is when a person with bad intentions sends you a message via email, text, or a social media post wanting you to click a link or respond with information.
How do you know it is a phishing scam?
Phishing scams can all look different on the surface but they all have a general approach that can include the following:
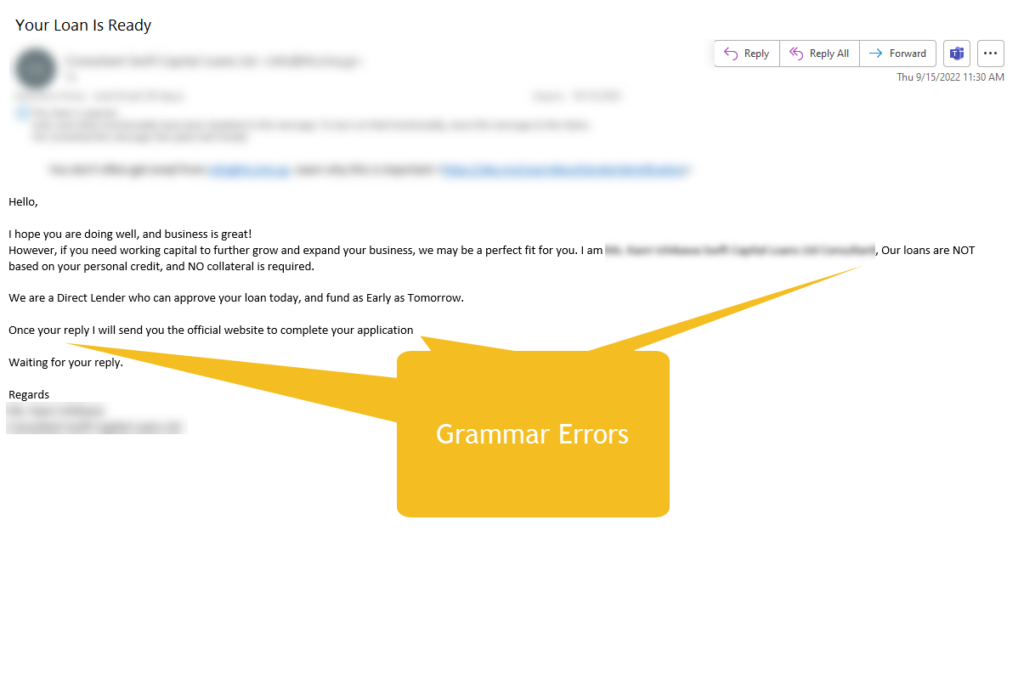
- It has a very urgent tone.
- It may contain spelling or grammar errors.
- It is not directly addressed to you in the body or to block of the message.
- It requests you to send personal or sensitive information.
- Reports are surfacing that hackers intentionally use poor grammar or spelling. If someone comes their way via a message that has these errors, they are a more gulllible candidate for a cyber crime.
Phishing Emails and Hyperlinks
If you ever received a phishing emails and it contains hyperlinks you can try this technique to uncover its destination but also know hackers have new ways to MASK the web address.
SPECIAL NOTE: Bank and Financial Emails
If you received an email from your bank or financial institution and it appears to be a scam, they all recommend visiting the website directly by typing it into your web browser and then using your account to contact them through the private messaging. You typically will not receive an email asking you to do anything with clicking links.
ACTION STEPS TO TAKE:
- Hover over the hyperlink in the email but do not click it.
- Look at the popup or the status bar for the full web address.
- Does the address appear with a very cryptic address or does it appear legitimate?
- If it is cryptic or shortened read below.
HOWEVER… Even if it looks like it came from a legitimate sender, you want to still verify it. Visit legitimate website and contact them through it.
Tips on verifying email links and attachments
Phishing is getting more sophisticated but so are the tools to debunk them. These are some that are available to you. If you encountered a shortened link or confusing or encrypted links these can help you uncover them.
A SHORTENED LINK (e.g. Bitly)
A shortened web address can be used to to hide a very long web address and keep a message short. These shortened addresses can mask a bad link.
How to use it:
- Copy the link.
- Then visit the CHECK OUT SHORT URL (http://checkshorturl.com) where you can uncover the actual destination.
STRANGE LOOKING LINKS
Some hackers send emails with very odd, encryptic links. When these links are cliked they can send you to websites where they can gather personal information or you can download malicious software.
How to use it:
- Copy the long cryptic link.
- Then visit URL DECODE AND ENCODE (https://www.urldecoder.org) where you can then uncover the destination and determine if it is ok.
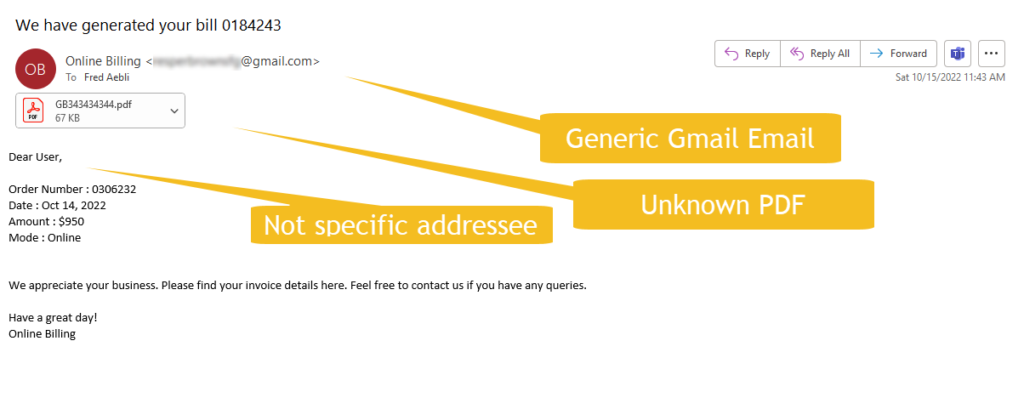
FILE ATTACHMENTS
Avoid opening attachments from senders you do not recognize. They can be a way to download malicious software or send you to a website where you download malicious code.
What to do when ...
You CLICKED a link in a phishing email
Don’t panic. Take action with these steps.
- Disconnect the device from the internet.
- MOBILE DEVICE: Put it is AIRPLANE mode.
- Laptop/Desktop: Disconnect from the internet by “FORGETTING” the network from your list or unplugging the network cable. This helps avoid any impact on your data stored on your device.
- Contact by phone or via your online account the bank, credit card company, etc.. Use the phone number on a statement and NOT the one in the message.
- Backup your files
- REPORT THE INCIDENT (contains a number of resources).
You IDENTIFIED a link in a phishing email
Good job. Now do the right thing and repot it. Too many incidents go unreported and the threat is allowed to continue and possibly evolve.
- REPORT THE INCIDENT (contains a number of resources).
How to protect ...
Note that the threat is an evolving one and you want to also remember to change your protective measures as needed.
Remember to not just use ONE of these but incorporate all of them as a layered security approach.
- Stay informed about recent phishing techniques.
- Use a SPAM filter.
- Enable your browser to prevent fraudulent websites.
- Keep your web browser up to date.
- Always contact the company when prompted to enter account details online.
- Inspect the URL for the “HTTPS”. This indicates a Secure Socket Layer. Eventually, all websites will be required to have this.
Phishing on social media and text messages
The rules with email phishing also applies to social media messages and posts and text messages.
If you click a link and then are redirected to LOGIN where you would then use your login and password, DO NOT ENTER YOUR INFO.
Be smart. Sharing personal information through prompts on social media can be an attempt to gather information pertaining to your login or password. Don’t respond to these question type posts if you do not know who is posting them.
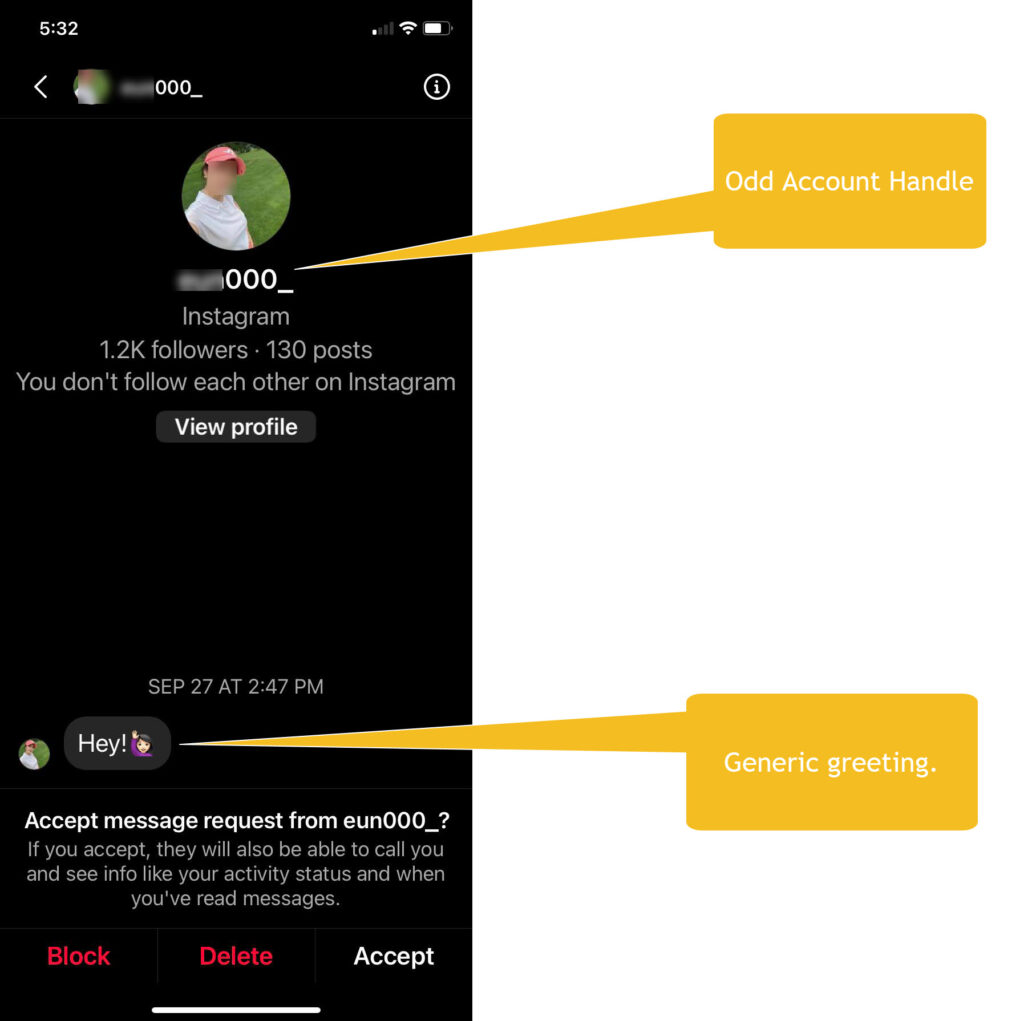
ACTION STEPS TO TAKE:
- Do not reply to the sender.
- Verify the account from which you are geting the message or request.
- If it is not legitimate, BLOCK the sender.
- REPORT THE INCIDENT (contains a number of resources).
HOWEVER… Even if it looks like it came from a legitimate sender, you want to still verify it. Visit legitimate website and contact them through it.
Realize anyone can get phished. It isn’t just for someone new to the internet. I can share I accidently responded to a well crafted email that contains information that seemed like it knew me.
Cybersecurity isn’t a one thing only practice. Security is a layering approach and it starts with being informed. Please be sure to pass along this information for others so they can #BeCyberSmart.
Happy coding and be safe online!

Mr. Fred
Let Me Help You

If you are a teacher or someone looking to help others learn to code, let me help you.